Apigee Integration Overview
How does Ubiq Work on Apigee?
Architecturally, the Apigee integration is built upon our Java SDK and the architectural concepts that we introduced in our data analytics integrations of an “offline mode” aimed at supporting environments that are gray- or black-box and are transactional (like running a query or processing an API request.) The integration is intentionally designed to be an integration that is no-code and fits into the Apigee topology and support structure.
At a high level, the Ubiq Apigee components deploy shared workflow pieces to your Apigee environment that allow for invoking encrypt/decrypt operations and manage key caching. The overall flow of your data and APIs do not change, but you’ll see a number of new steps in your Apigee workflows where the API request/response gets modified based on your encrypt/decrypt configuration. The detailed steps of the Ubiq-modified Apigee workflows use these pieces:
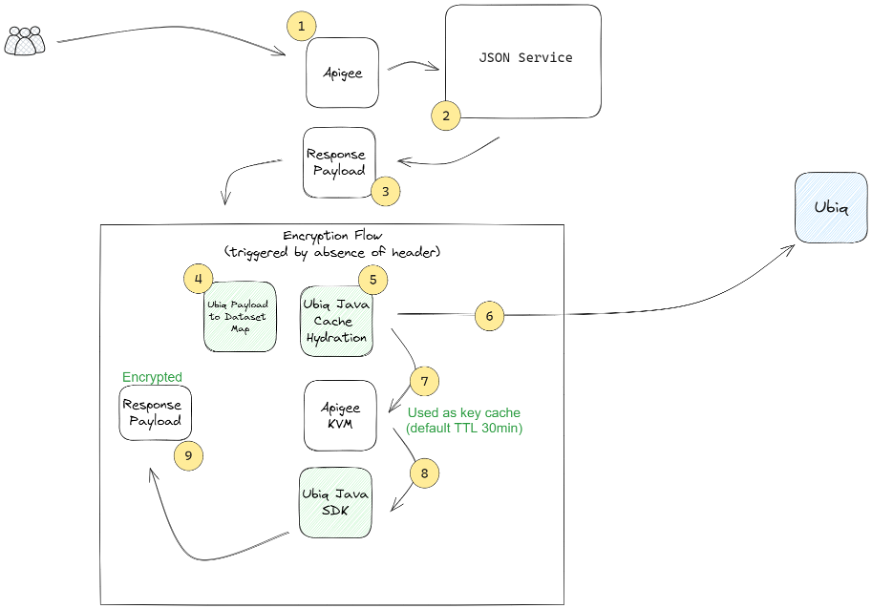
The only component that makes an outbound call to Ubiq is the #5 (cache hydration), which is a prerequisite step and not executed unless the cache is expired (it is not executed per API request.) This architecture keeps the incremental impact to performance < 60ms to decrypt/encrypt ~ 50 data elements in a payload.
Example Use-Case: Using to Encrypt Sensitive Payload of an API
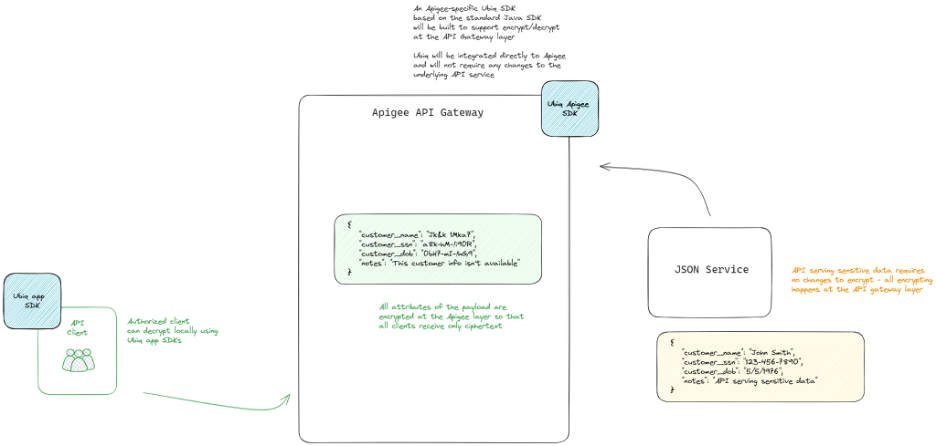
Encrypting or decrypting data at the API Gateway layer can be used in a bunch of different ways to protect data as it flows in or out of your systems. One of the more common use-cases we see is to protect data leaving your environment where you know that data is either not used by the downstream client or does not need to be used in plaintext (i.e. its okay to have the sensitive data masked/encrypted in the downstream client.) As an example flow, our standard Apigee integration can be used as-is, with a simple configuration to map your Ubiq dataset(s) to the attributes of the payload you’d like to encrypt (see Mapping dataset name to the json fields to encrypt for mapping examples.)
Data gets encrypted as the API response leaves your environment without changing any code in the underlying API.
Apigee vs. Other Ubiq Libraries
It’s all the same - the Apigee integration and its encrypt/decrypt is completely cross-compatible with all of the other libraries and languages.
All of the same features and values still hold true for using Ubiq on Apigee:
- Data never leaves your environment to encrypt or decrypt data
- No changes needed to your underlying APIs - you can add encryption or decryption without changing code
- Encryption/decryption can happen as the data enters or leaves your environment - protecting it from any subsequent access
- No key management required - just like our application library usage, keys “follow the data” and are managed in the Ubiq SaaS UI for seamless key rotation and revocation
- Flexible access controls; Ubiq API keys are used to authenticate the Apigee workflow to Ubiq
- Flexible key association - your key and dataset design in the Ubiq SaaS UI can enable granular key usage (like a unique key per attribute) without any implementation complexity - your Apigee dataset mapping configuration tells the systems everything it needs to know
- Cross-library compatibility - our Apigee library uses the same NIST-approved structured (format-preserving) encryption algorithm, so you can encrypt/decrypt with Apigee and then encrypt/decrypt with any other Ubiq library
Summary & Highlights
- It is self-contained to Apigee and does not require any special add-ons, licenses, or customizations
- Data never leaves your environment to encrypt or decrypt - the actual crypto happens in Apigee itself
- No encryption knowledge required to implement … configuring encryption is done by a simple Apigee workflow template (and we give you an example)
- Implement-once, use-many design; once you’ve added the Ubiq integration to Apigee, you can invoke it with a few simple configurations in any of your APIs and individual rules for specific payloads can be made for each
- Total performance impact is < 60ms to encrypt ~ 50 data elements in a payload
- Cross-compatible encryption/decryption with every other Ubiq library, so you can encrypt/decrypt with Apigee and then encrypt/decrypt upstream at a client or downstream in a database or application
- Total feature parity - including key management and key rotation features delivered and managed through the Ubiq UI
- No key management required - just like our application library usage, keys “follow the data” and are managed in the Ubiq SaaS UI for seamless key rotation and revocation
- Flexible access controls; Ubiq API keys are used to authenticate the Apigee workflow to Ubiq, and that gives access for Apigee to interact with Ubiq and encrypt
- Flexible key association - your key and dataset design in the Ubiq SaaS UI can enable granular key usage (like a unique key per table, per column or per Snowflake database) without any implementation complexity
Updated 11 days ago
