Entra IDP Integration
Step-by-step instructions for Entra ID Integration

IDP Integration
IDP Integration setup UI is available on the account page (#/profile) for all enterprise plan users.
Setting up the IDP integration has 2 parts:
- Configuration of a new SCIM integration that synchronizes users and groups from your Entra to Ubiq
- Configuration of a new Entra application that allows Ubiq to verify and work with your Entra tokens
Auto-provisioning
API keys are provisioned that correspond to each SCIM-sync'd user account and permissions for those API keys are associated to Datasets within Dataset Groups that have a matching SCIM-sync'd group.
When | Provisioning Logic |
|---|---|
IDP user is created |
|
IDP user field change | Rename API Key if auto-provisioned |
IDP user active field changed | Enable/disable API Key as appropriate |
IDP user is deleted | Delete API Key |
IDP group created | Do nothing |
IDP group members are changed | Provision access for the user API Key to all datasets in the matching Dataset Group |
IDP group display_name field changed | Remove access for the user API Key to all datasets in the old matching Dataset Group |
IDP group deleted | Delete all corresponding API Key access to the matching Dataset Group |
Dataset creation (in Ubiq UI) | Provision access to the dataset to API Keys if it is in a matching Dataset Group |
Dataset → Dataset Group Assignment (in Ubiq UI) | Provision access to the dataset to API Keys if it is in a matching Dataset Group |
Note: The editing of auto-provisioned API Keys will be disabled in the UI
Ubiq IDP Integration Setup
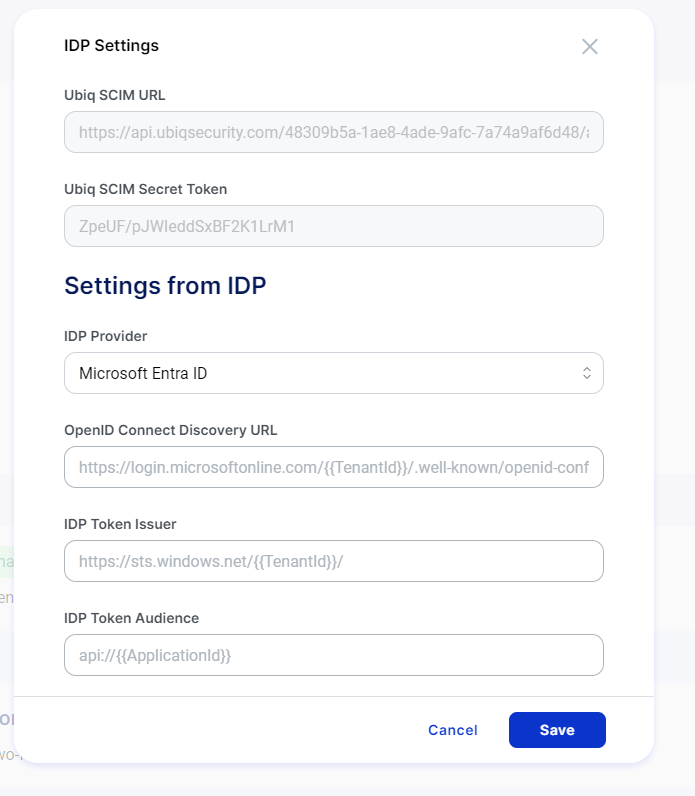
When enabling IDP Integration the following settings will need to be populated from values in Microsoft Entra ID
Azure AD / Entra Integration
Create Enterprise Application
- Microsoft Entra ID Dashboard → “+ Add” → Enterprise Application
- Click “+ Create Your Own Application”
- Enter desired name of the Application
- Select “Integrate any other application you don’t find in the gallery (Non-gallery)
- Click Create
Users / Groups
- Users & Groups → “+ Add user/group”
- Select users or groups that should be allowed to access Ubiq
- Click Assign
$
Provisioning
- Provisioning → Provisioning
- Change Provisioning Mode to Automatic
- Set Admin Credentials Tenant URL = Ubiq SCIM URL from Ubiq IDP Integration screen
- Set Admin Credentials → Secret Token = Ubiq SCIM Secret Token from Ubiq IDP Integration screen
- Click Test Connection
- Click Save
Configure Application
- Microsoft Entra ID Dashboard → App registrations → All Applications → Your Application
Enable Access Tokens
- Authentication → Check “Access tokens (used for implicit flows)” → Save
Client Secret
- Certificates & secrets → Client Secrets → “+ New client secret”
- Enter description of client secret (e.g. Ubiq Secret) and desired expiration
- Click Add
- Copy new secret value and store somewhere safe, will be used later by client library
Token Claims
- Token configuration → “Add groups claim”
- Select desired group types, likely the “Groups assigned to the application” option
- Click Add
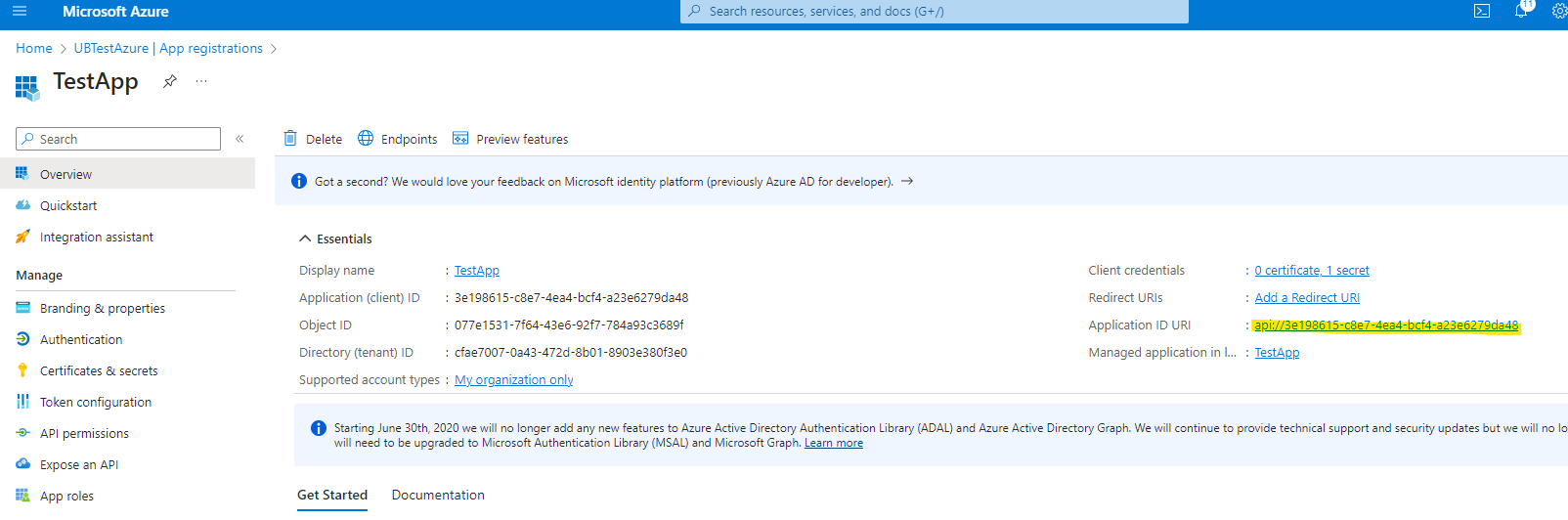
API Scopes
- Expose an API → “Add” Application ID URI
- Click Save
- Click “+ Add a scope”
- Scope name => Custom.Read
- Who can consent? => Admins Only
- Enter desired display names/descriptions
- Click Add scope
API Permissions
- API permissions → “+ Add a permission” → “APIs my organization uses”
- Select your application name
- Select Custom.Read permission
- Click “Add permissions”
- “+ Add a permission” → Microsoft Graph
- Click delegated permissions
- Select offline_access, openid, and profile permissions
- Click “Add permissions”
- Click “Grant admin consent for YourAzureADTenantName”
- Click Yes to confirm
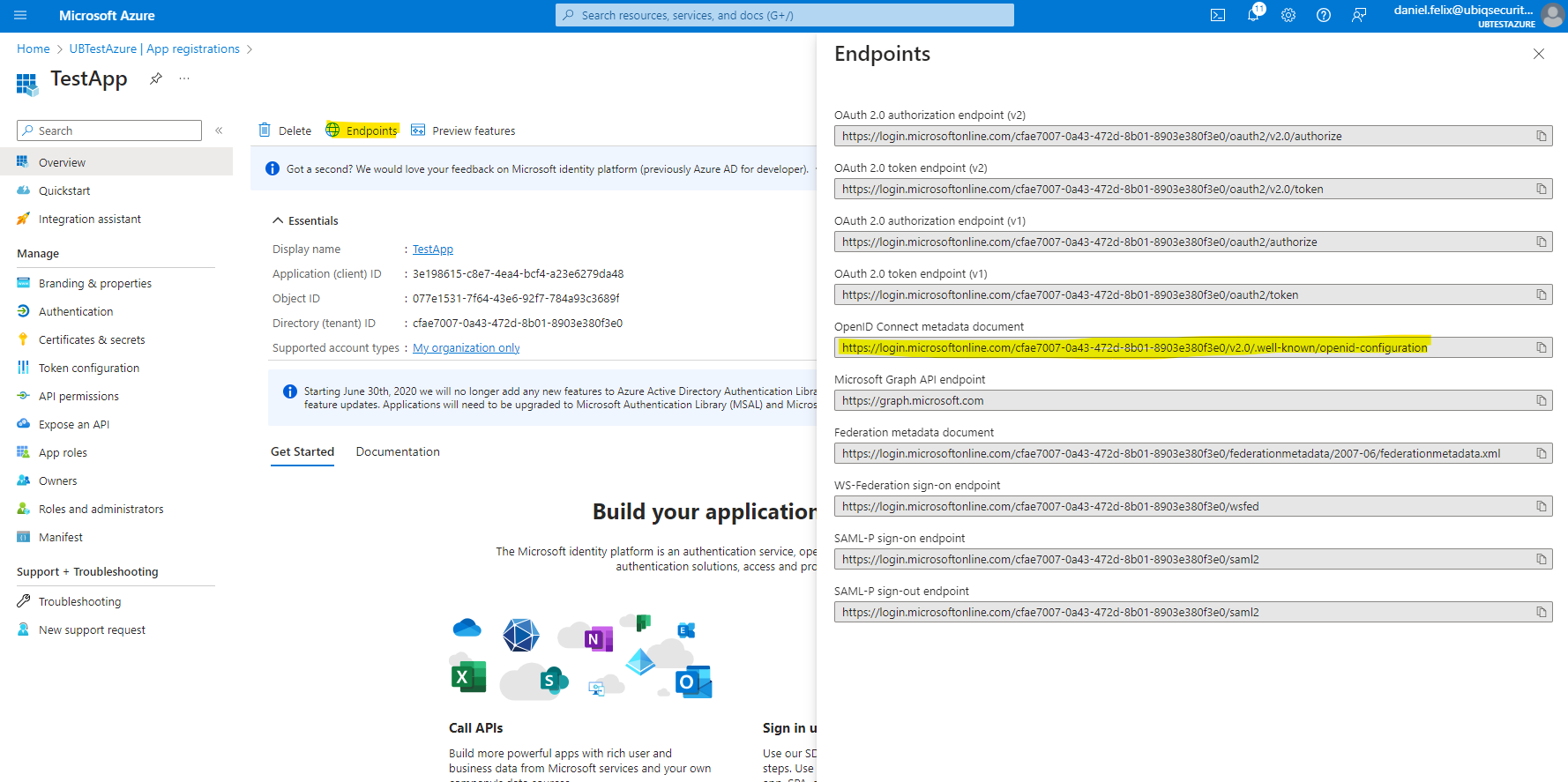
OpenID Connect Discovery URL
Microsoft Entra ID Dashboard → App registrations → All Applications → Your Application → Endpoints → OpenID Connect metadata document
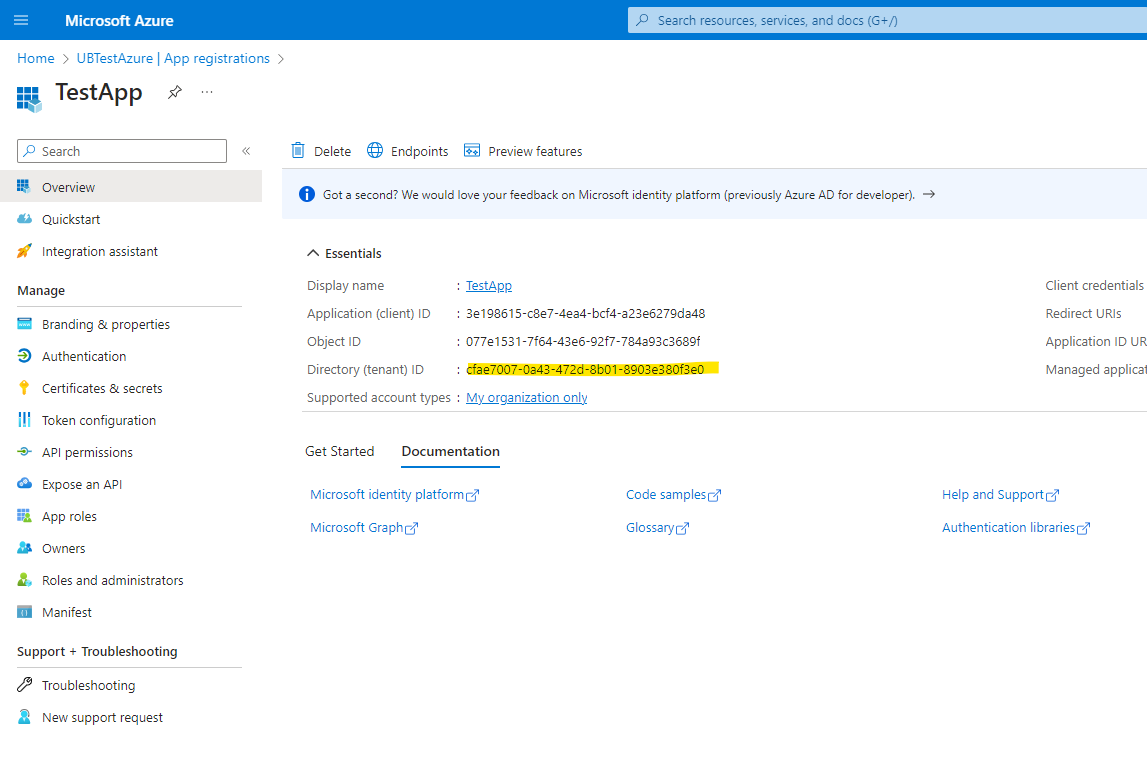
IDP Token Issuer
Value is https://sts.windows.net/TENANT_ID/ and your TENANT_ID can be found at Microsoft Entra ID Dashboard → App registrations → All Applications → Your Application → Directory (tenant) ID
IDP Token Audience
Microsoft Entra ID Dashboard → App registrations → All Applications → Your Application → Application ID URI
Updated 5 months ago
